In-depth Hunter IO Review: Enhancing Your List Building Method
Hunter IO Evaluation: Enhancing Your Email Browse Performance
Seeker IO arises as an appealing option for enhancing this process, providing a suite of tools created to improve email search efficiency. From its Email Finder tool to Projects function, Seeker IO presents a robust set of capabilities intended at enhancing email-related tasks.
Features of Seeker IO
The attributes of Seeker IO provide customers with beneficial devices for enhancing email search performance. One essential feature is the Email Finder, which permits customers to go into a domain name and obtain a listing of e-mail addresses related to that domain. This attribute streamlines the process of discovering get in touch with details for experts within a specific business. Furthermore, Hunter IO provides Email Verifier, a tool that helps customers make sure the validity of e-mail addresses before sending out messages. This can assist reduce bounce rates and boost general e-mail deliverability.
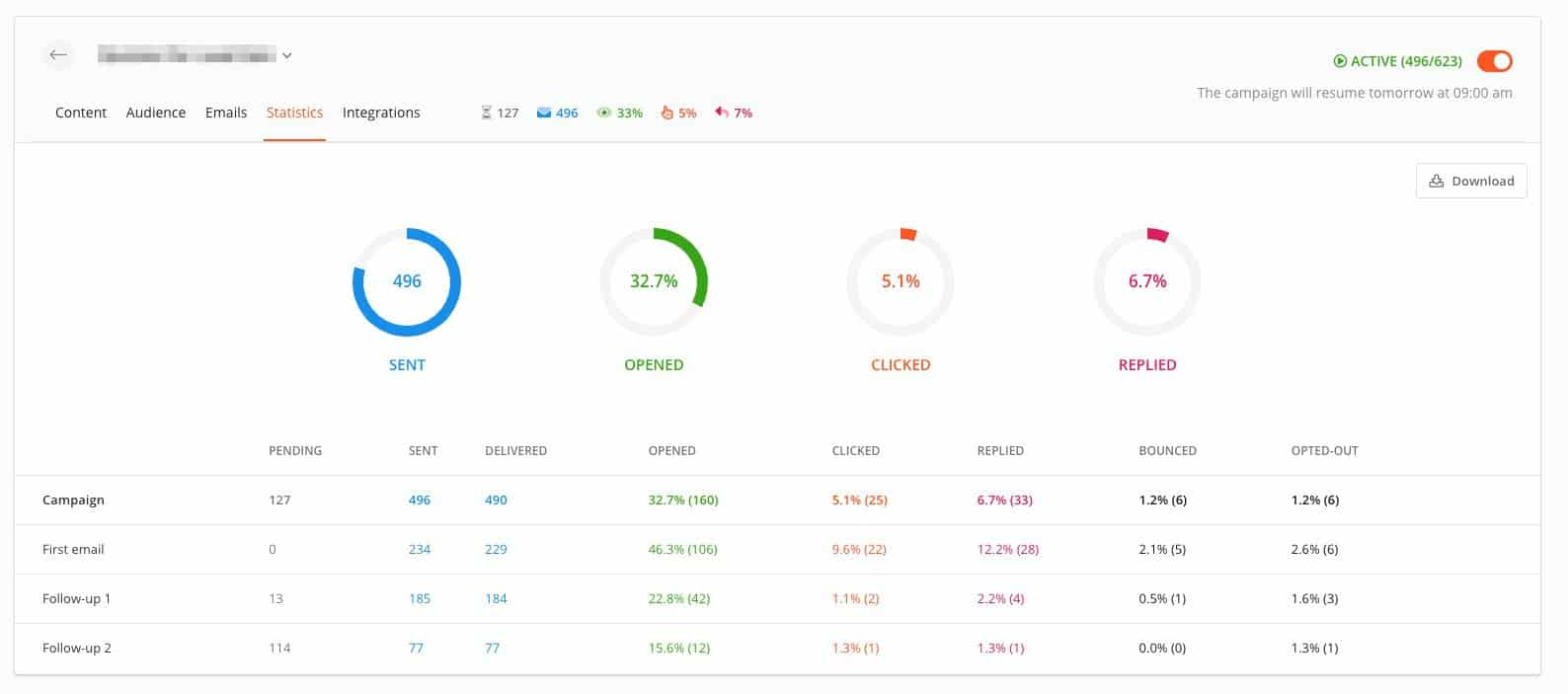
An additional important attribute is the Campaigns device, which enables individuals to arrange and track their e-mail outreach efforts successfully. Users can develop customized email projects, established up automated follow-ups, and monitor reactions all within the system. This feature is particularly beneficial offer for sale professionals, marketers, and recruiters who count on email communication to reach their targets.
Moreover, Seeker IO gives a Chrome expansion that incorporates perfectly with customers' browsers, permitting quick access to email search abilities while surfing the internet. This expansion boosts customer experience by giving on-the-go access to Hunter IO's attributes without the requirement to change between applications or tabs.
Just How Hunter IO Works
Successfully promoting e-mail search procedures, Seeker IO operates by leveraging innovative algorithms to check domain names and recover appropriate email addresses related to them. The system functions by permitting individuals to input a domain, complying with which Seeker IO's algorithms carefully creep with the internet to remove email addresses linked to that domain name. This scanning process is automated and swift, enabling individuals to obtain precise contact information successfully.
Additionally, Seeker IO utilizes various methods to verify the precision of the extracted e-mail addresses, guaranteeing a high deliverability price. By cross-referencing data from several resources and utilizing domain confirmation tools, Hunter IO boosts the dependability of the given email addresses. This verification procedure help users within their desired recipients efficiently, consequently improving interaction initiatives.
Additionally, Seeker IO supplies users the choice to do bulk searches, enabling them to draw out numerous e-mail addresses concurrently. hunter io review. This attribute is especially useful for organizations and professionals who require call info for countless individuals or companies. Generally, Seeker IO streamlines the email search procedure, making it a valuable tool for enhancing efficiency and performance in getting to bent on contacts
Benefits of Making Use Of Seeker IO
Enhancing e-mail search capabilities via efficient processes and innovative formulas, utilizing Seeker IO offers a multitude of advantages for users in numerous markets. By automating the email browsing procedure, individuals can quickly access relevant get in touch with information without investing hours manually scouring the web.
Furthermore, Seeker IO provides a high degree of accuracy in its e-mail search engine result. The system's advanced formulas make certain that the offered e-mail addresses are legitimate and updated, decreasing the chances of bounced e-mails or stopped working deliveries. This integrity is critical for keeping a positive sender track record and guaranteeing that vital communications reach their desired recipients.
Additionally, Seeker IO enhances outreach methods by offering individuals with valuable insights right into their target audience. By getting to exact contact info, organizations can tailor their e-mail projects better, causing increased engagement and higher conversion prices. In general, the advantages of making use of Hunter IO prolong beyond straightforward e-mail search capabilities, providing customers a comprehensive option for maximizing their interaction initiatives.
Combinations With Seeker IO
Incorporating Seeker IO with various systems and devices improves the general performance and effectiveness of e-mail search procedures for users. By seamlessly integrating with popular platforms like Google Sheets, Salesforce, and HubSpot, Seeker IO enables individuals to directly access its email finding abilities within these tools. This assimilation streamlines the workflow, removing the demand to switch over in between numerous applications and saving important time. Furthermore, Seeker IO's API integration makes it possible for customers to automate the e-mail search process, making it more convenient and lowering hand-operated initiatives.
For marketing and use this link sales groups, integrating Seeker IO with client relationship monitoring (CRM) systems like Salesforce boosts list building activities by giving accurate and current e-mail addresses. This assimilation makes certain that outreach efforts are targeted and effective, bring about enhanced conversion prices. Furthermore, incorporating Hunter IO with outreach devices like click to read more Mailshake or Outreach.io enables individuals to flawlessly integrate validated email addresses right into their campaigns, boosting the possibilities of getting to the best audience efficiently. In general, these assimilations improve the capability of Seeker IO and optimize e-mail search processes for individuals throughout various markets.
Prices Choices and Plans
Amongst the essential factors to consider for individuals examining the Hunter IO solution is the series of prices choices and plans offered - hunter io review. Hunter IO offers a variety of strategies customized to fit different user demands, varying from the Free plan, which offers limited accessibility to functions, to the Enterprise strategy, providing substantial performances for bigger organizations
The Free plan permits individuals to perform as much as 50 totally free searches per month, making it ideal for individuals or local business with periodic email search demands. For advanced features such as bulk searches, email confirmation, and accessibility to extra information points, users can choose the Beginner, Growth, or Pro strategies, which provide increased search limitations and boosted capabilities.
For ventures seeking an extensive email search service, the Venture plan supplies custom prices based upon certain requirements, including API accessibility, devoted assistance, and progressed functions for reliable email outreach projects. By using a range of prices alternatives and plans, Hunter IO makes certain that users can select a bundle that straightens with their budget and usage requirements.
Conclusion
Finally, Seeker IO provides an extensive solution for boosting email search efficiency with its powerful functions, advanced algorithms, and seamless assimilations. By automating the procedure of finding and verifying e-mail addresses, Hunter IO conserves time and enhances outreach approaches for customers. With numerous rates strategies to suit various needs, Seeker IO is a useful tool for enhancing interaction initiatives and increasing performance in email search jobs.
The features of Seeker IO offer customers with important tools for maximizing email search performance. One essential attribute is the Email Finder, which allows individuals to go into a domain name hunter io review and receive a listing of e-mail addresses associated with that domain name. Additionally, Hunter IO supplies Email Verifier, a tool that aids users ensure the credibility of e-mail addresses prior to sending messages.Effectively helping with e-mail search processes, Hunter IO runs by leveraging innovative algorithms to scan domain names and obtain pertinent email addresses connected with them. The system's advanced algorithms make sure that the provided email addresses are legitimate and up-to-date, minimizing the opportunities of bounced emails or stopped working deliveries.